Home
Graphics
Tescrypt.B Report
Over the last few days I've been analyising a malware sample known as Tescrypt.B.
For this analysis we will be looking into Tescrypt.B under a Windows 7 VM.
Why Windows 7?
When ran through Windows 10 Windows Defender will detect, block, and remove Tescrypt.B.
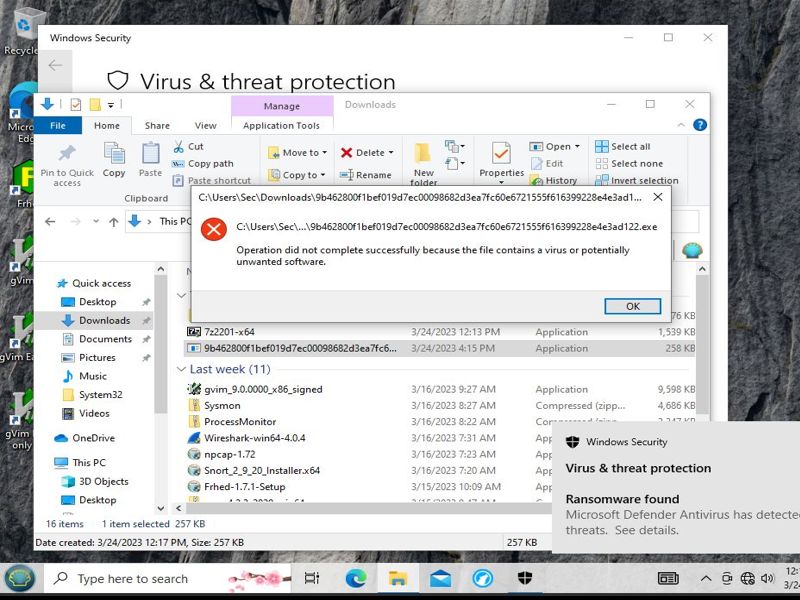
Windows 7 on the other hand will not detect Tescrypt.B at all even after encrypting all files.
For this reason Windows 7 will be the VM used.
Software Used During Analysis
As far as software goes the tools used are a fhred, notepad, and command prompt.
Notepad was used to show the files were encrypted as well as what the added files were saying.
Fhred is a hex editor that was used to figure out the commands being ran.
Command prompt was used to remove the maleware.
Startup of Tescrypt.B
Upon downloading the program doesn't begin until the user runs the program in question.
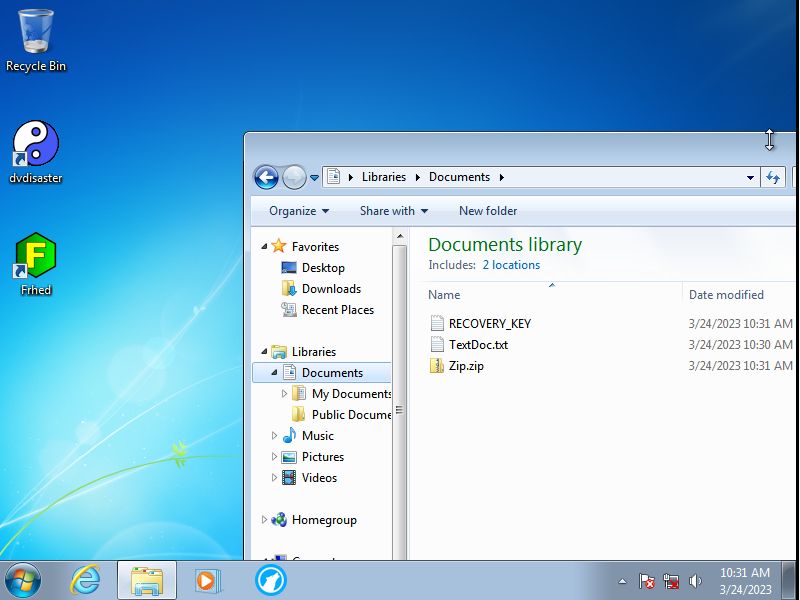
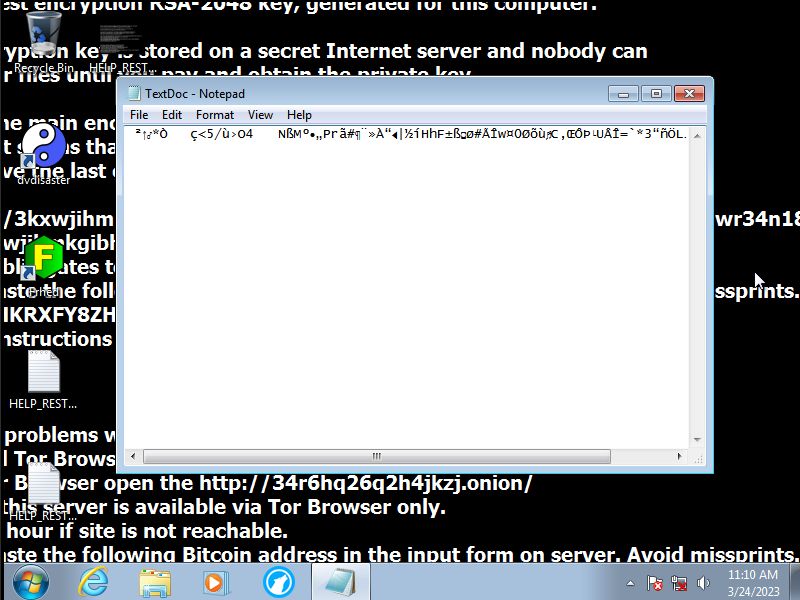
Once the program has been ran the first thing it will do is add a file called RECOVERY_KEY.txt to the Documents folder which contains a possible
recovery key for the files.
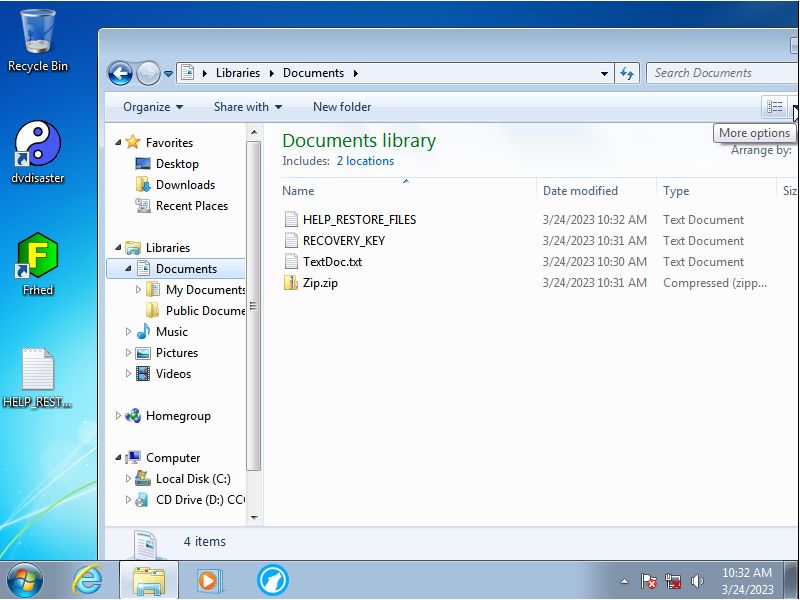
Aftwards another file called HELP_RESTORE_FILES.txt will be added all over the computer.
A few seconds later the actual encryption itself happens, the background is replaced with a background called
HELP_RESTORE_FILES.bmp which is more or less
the same as the file added earlier, and a program called CryptoLocker
gets added which claims to have used RSA-2048 encryption and threatens the user with a 4 day time limit.
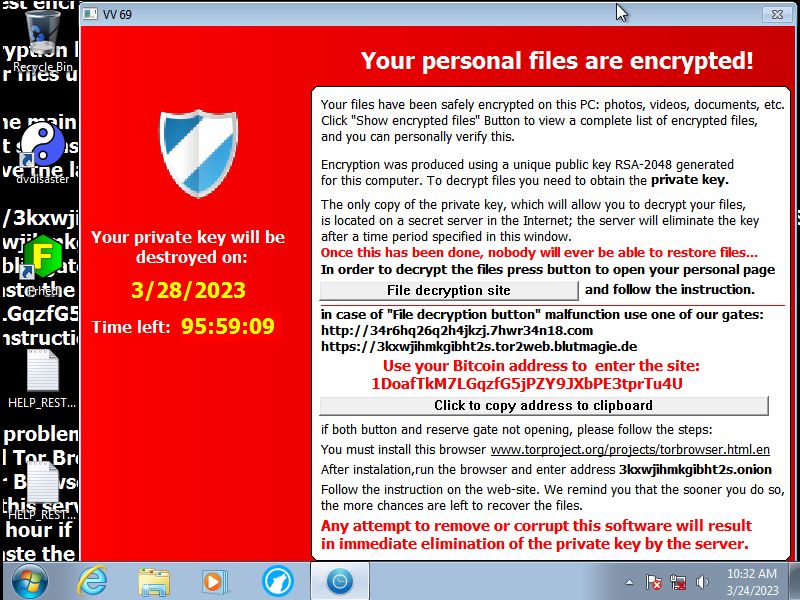
Effects of Tescrypt.B
Upon encryption most files are given an .ecc extension and is marked as an ECC File but adds an addtion . file extension of whatever
the oringinal file was. EX:Test.txt.txt.ecc
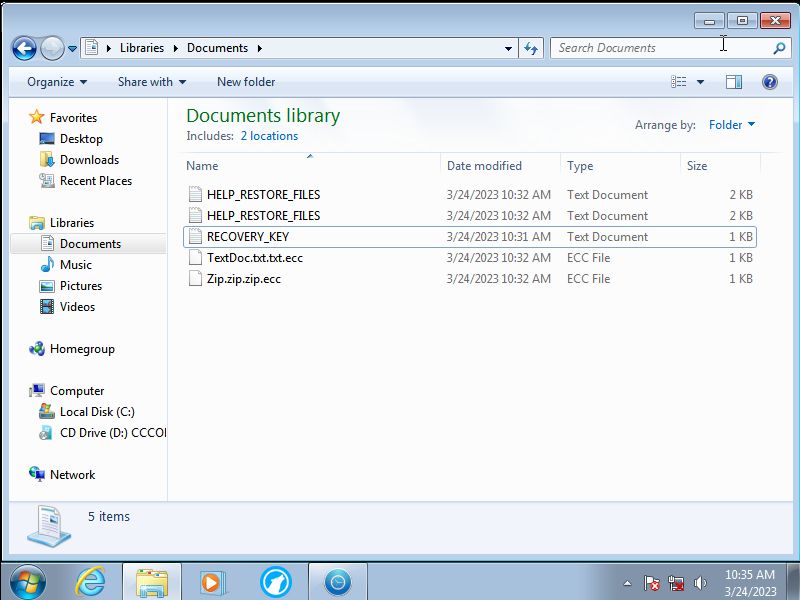
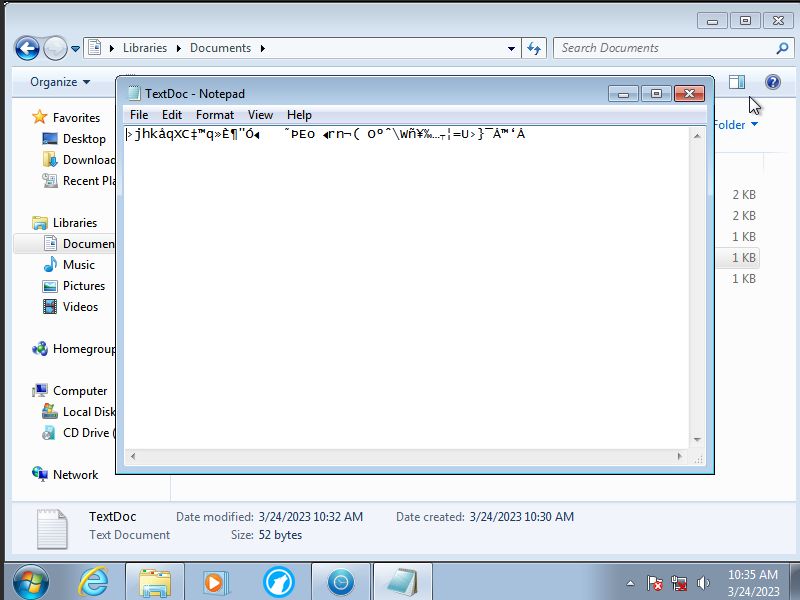
If the .ecc extension is removed it will be revealed that the text file was indeed encrypted and would be impossible to read.
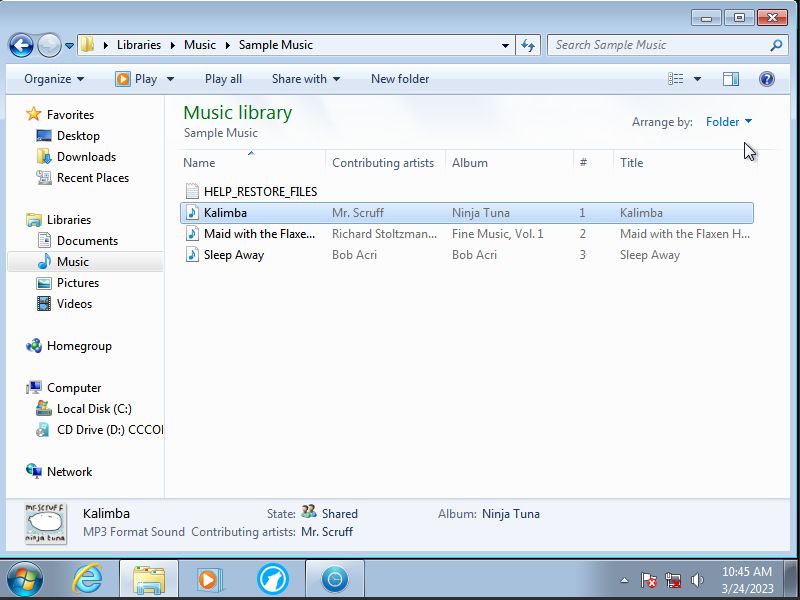
The same is true for most files, exept for music files for whatever reason don't seem to get encrypted at all.
Another thing Tescrypt.B does is prevents certain programs specificly command prompt and task manager from being ran at all.
The worst part of all of this is the fact that every time the user resets the system as long as the malware is running any files
added since will also be encrypted
on top of that the encryption key will reset itself meaning that even if the user did figure
out how to decrypt the file it would just reset itself anyway.
Tescrypt.B's Code
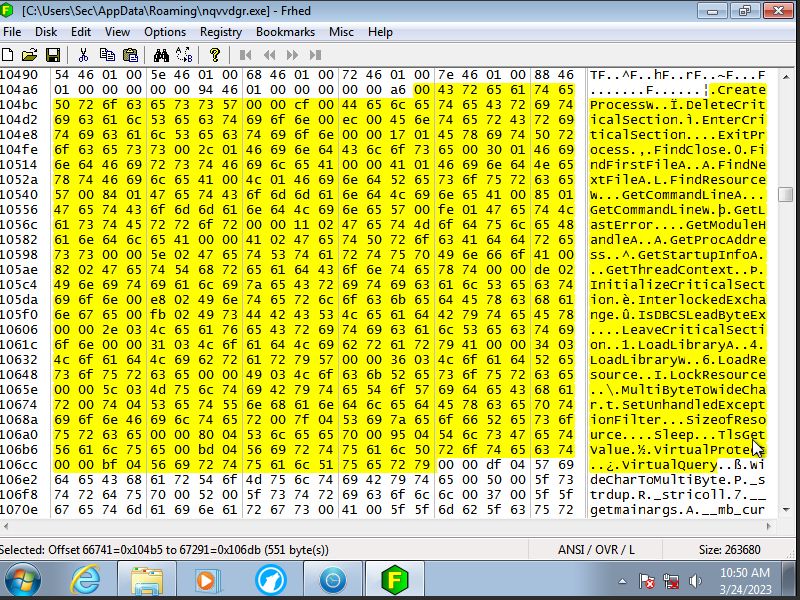
Looking at the actual code for Tescrypt.B a few things become apperent.
For starters Tescrypt.B will first gain access to the system memory.
After it has gained access to the systems memory it will then find all files owned by the user.
Next it will setup its own startup which will run every time the system restarts.
Once thats done it will load up the system memory with the info it has found.
Then the malware will corrupt the users files not encrypt meaning that the whole RSA-2048 thing was a scam.
Finally once thats done the process will repeat itself as long as the malware is runinng on the system.
Removing Tescrypt.B
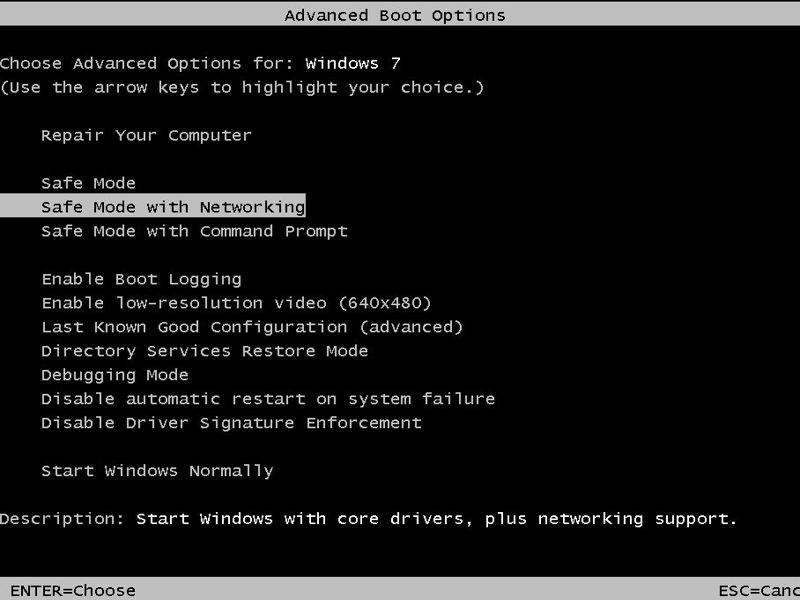
To remove Tescrypt.B first the user must go into safe mode by holding f8 on restart and selecting safe mode with networking.
Next the user must find the path to the exe file which will be in the roaming folder.
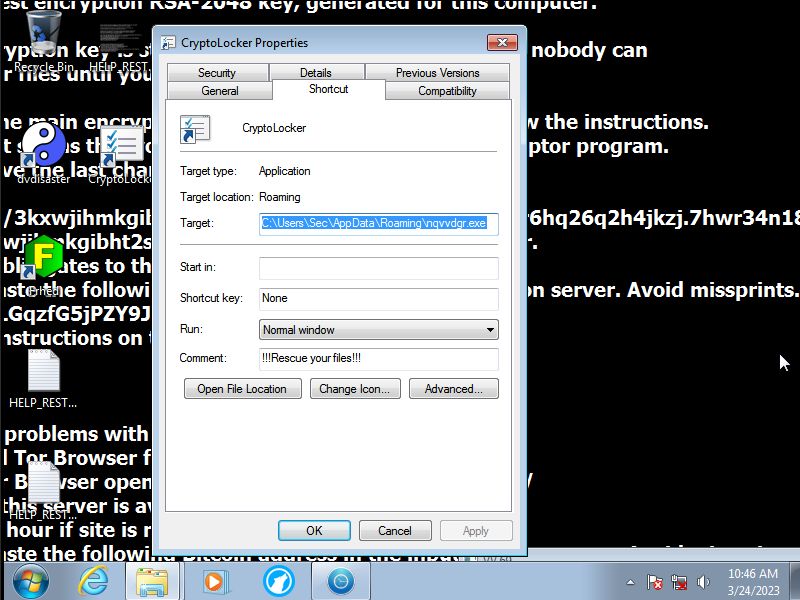
Looking in the roaming folder a few files will be found that were added the malware in question will be marked with
a blue clock icon name will be different every time.
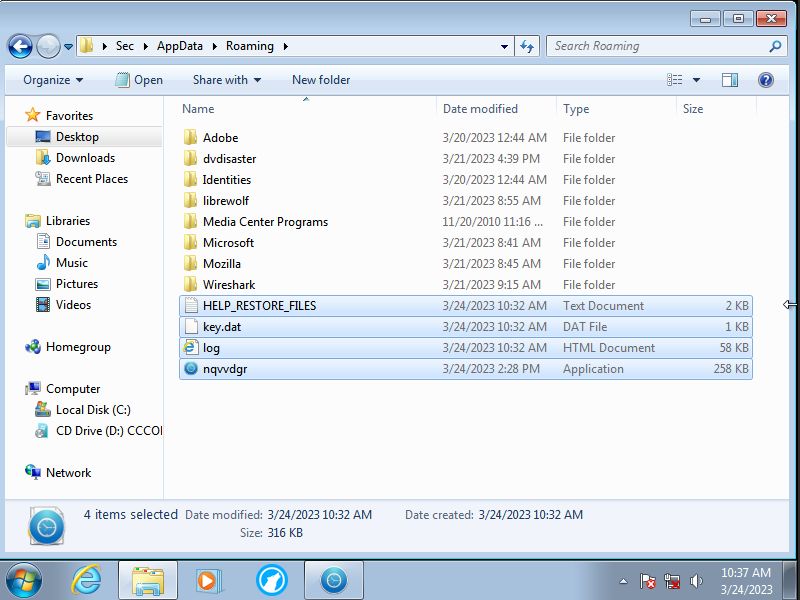
Go into the command prompt and type cd AppData cd Roaming del [exename].exe
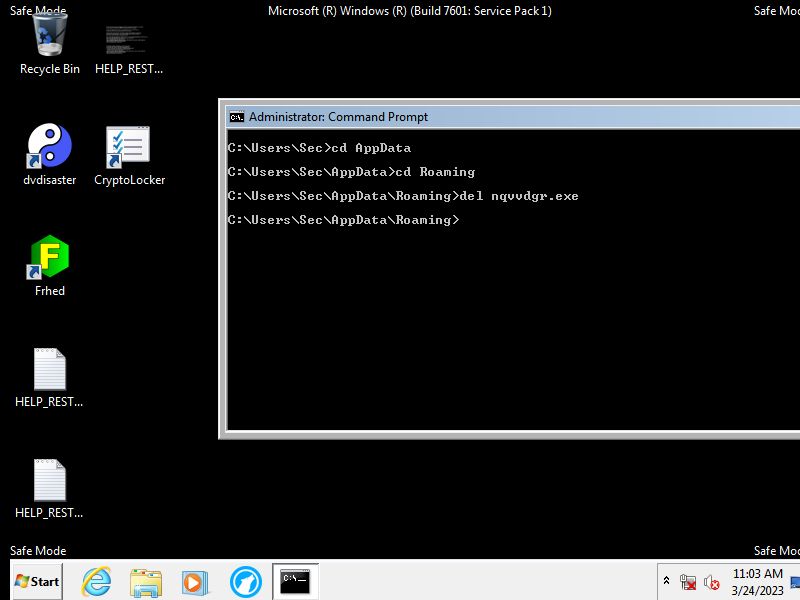
Also delete CryptoLocker while at it and the maleware is gone.
After Tescrypt.B's removal
The good news is that any new files created after removal won't get corrupted, the bad news is that this won't fix the files that
already have been corrupted.
What also won't go away is the fact that the HELP_RESTORE_FILES.txt file will still load up upon every restart.
At the very least though no further damage will be done to the system.
Take Aways
This malware does not actualy encrypt anything as the ECC file extension is most commonly linked to dvd errors
not encryption rather the malware straight up corrupts any files owned by the end user.
As long as the user is not using windows xp-8 the user should have no problems as defender will not allow the maleware
to run whatsoever.
I probably don't need to add this but keep a good backup of your files at all times incase anything like this were to
happen to your computer.
SHA256: 9b462800f1bef019d7ec00098682d3ea7fc60e
6721555f616399228e4e3ad122