Home
Graphics
Snakekeylogger Report
As if malware wasn't bad enough already we also have to deal with keyloggers as well.
For this analysis we will be looking at one sample of the SnakeKeyLogger family.
Software Used
For this analysis the software used includes the Frhed hex editor, the windows registry, and
a free download for windows 10 users being Process Monitor.
What is even going on here?
To the untrained eye it seems as though the system is running as normal despite the fact
that windows defender catches this threat and tries to remove it. However even though it seems as
though nothing is happening running process monitor shows us that this program is accessing
multiple dll files including but not limited to System.Core.ni.dll , Microsoft.VisualBasic.dll ,
System.ni.dll , mscorlib.dll , System.Configuration.ni.dll , System.Xml.ni.dll ,
System.Data.SqlXml.dll , bcrypt.dll , clr.dll , cryptsp.dll , rsaenh.dll , and cryptbase.dll.
It is unknown exactly what it is doing with these files, but it is very likely that it is
useing files like bcrypt.dll to steal any passwords that may be stored on the system
as well as any private keys that may be stored on the system in an atempt to break
the systems encryption.
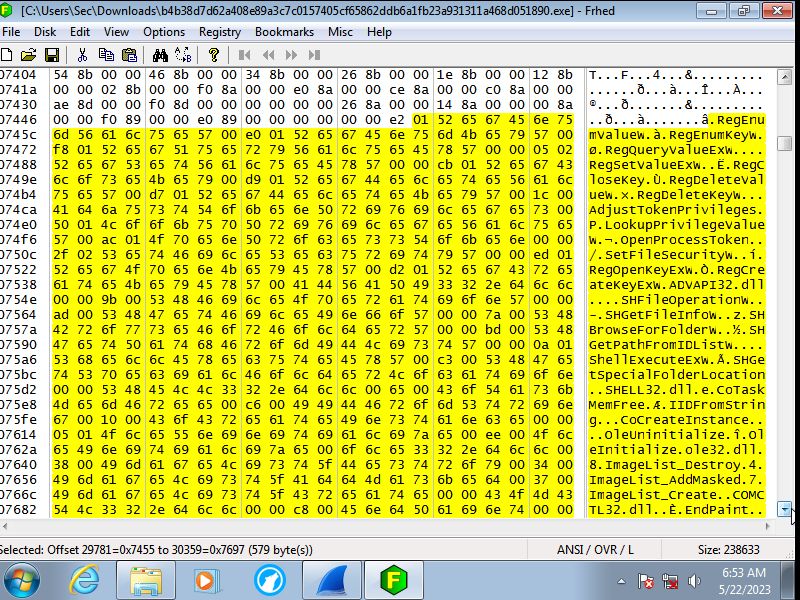
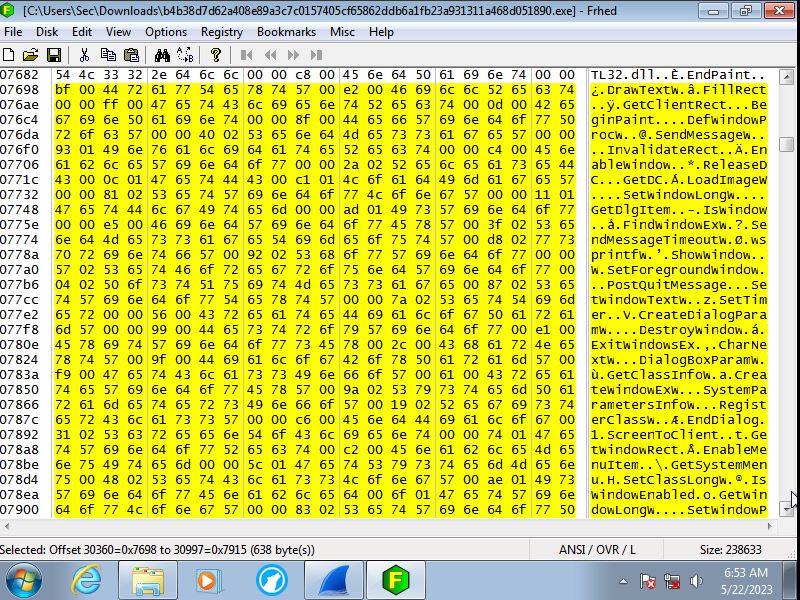
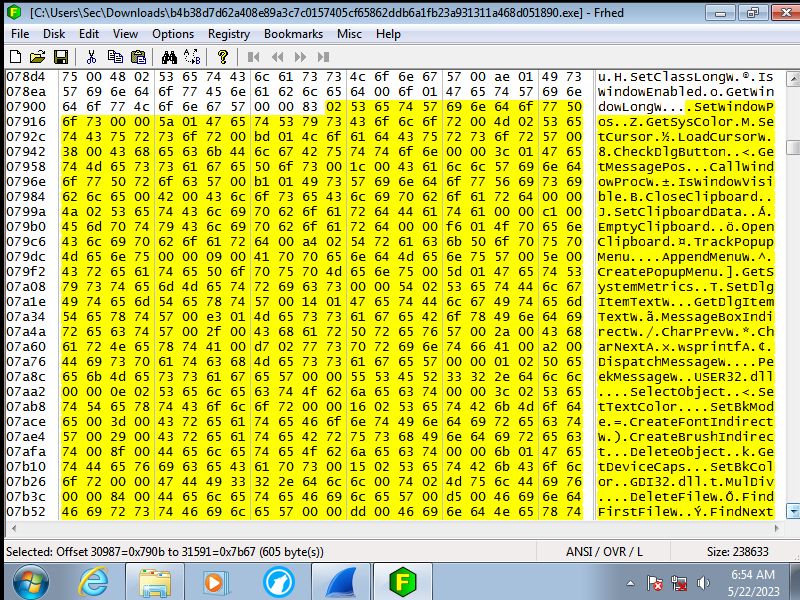
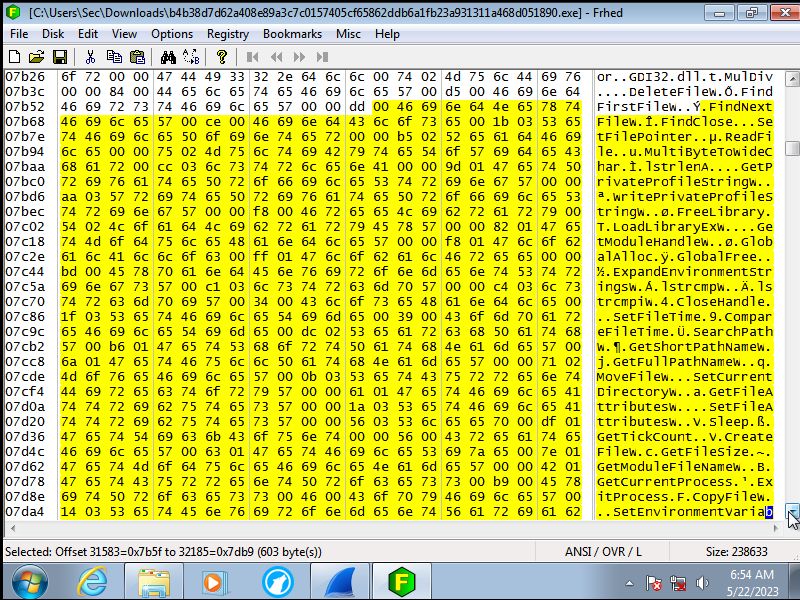
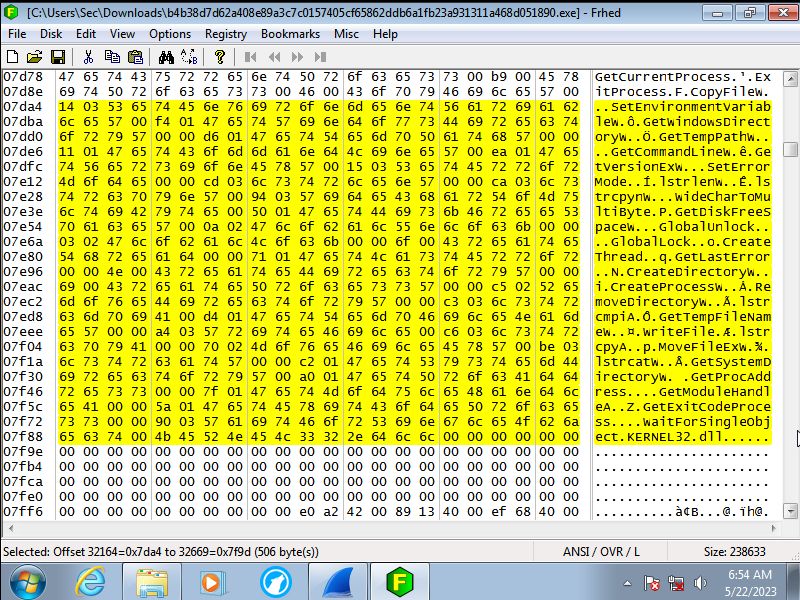
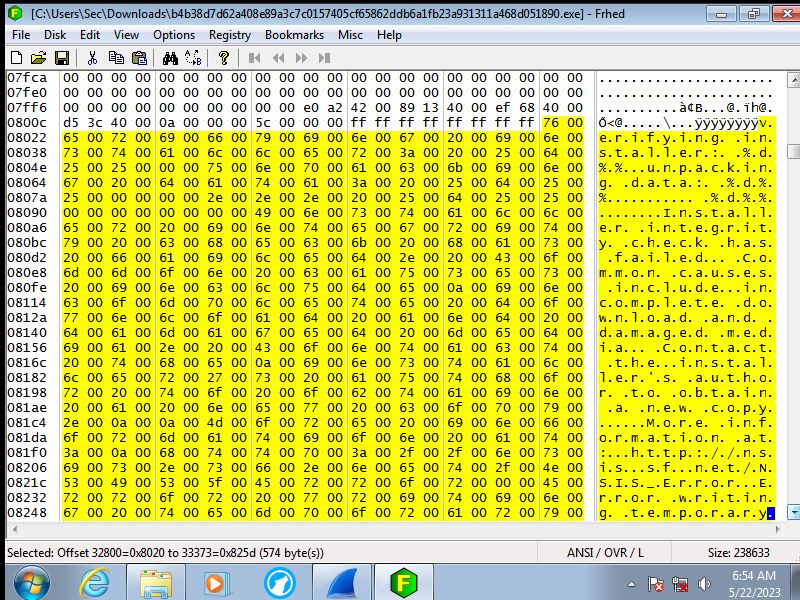
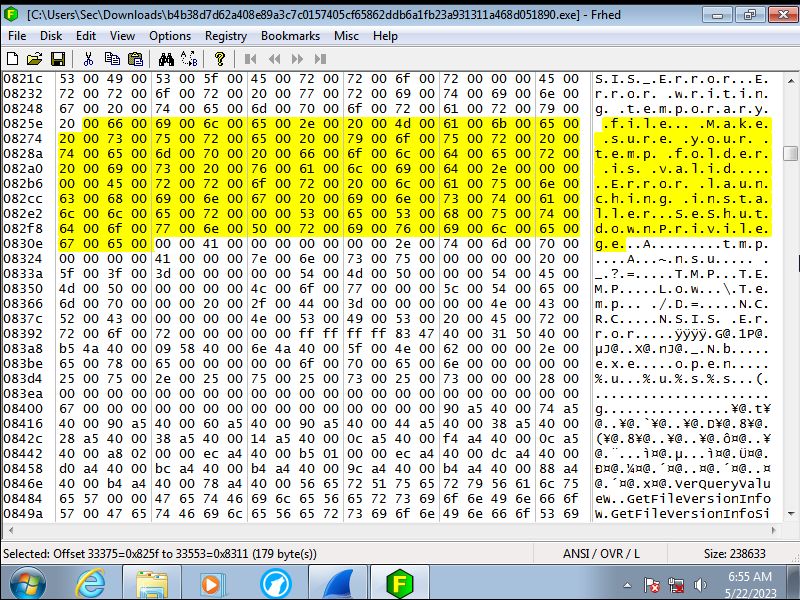
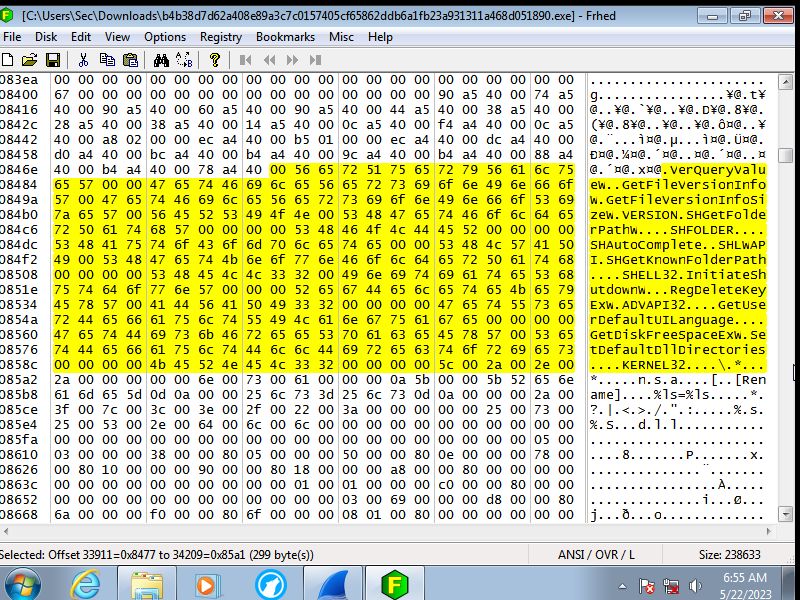
The code translated
Looking at the actual code it first accesses the registry to change premissions
to allow the keylogger to track what is being typed in. Then it will read what ever
it can to grab sensitve data that is already on the machine. This even goes
as far as to grab the system start time. Finally it will write in to the memory
to stay undetected by the end user essentialy injecting malicous code into
the systems memory so that even if the progam is removed the memory is still
sending this information back.
The intial progams location
Like alot of other malware this one prefers to hide in the Roaming folder in
C:\Users\username\AppData this time in a folder called swgplueajfo. Fortantly
it does not try to lock itself on the computer so removing it shouldn't be too
big of an issue.
Takeaways
It is clear that this keylogger falls into the Memory-injecting family.
While it is easy to remove the intial program the fact is that it has already
put malicous code into the memory itself therefore it is best to either boot
from a backup or reinstall the os. Moral of the story 1. even if it seems
like the malware is gone it could still be lurking out there on your system, 2.
Always backup your important files incase this were to happen.
Sha256:b4b38d7d62a408e89a3c7c0157405cf65862ddb6a1fb23a931311a468d051890